When moving your systems to the cloud, many security processes and best practices remain the same. However, you will encounter a new set of challenges that you will be required to overcome in order to maintain the security of your cloud-based systems and data.
To help you with this challenge, we’ve compiled a series of security best practices for cloud-based deployments.
Choose a Trusted Provider
The foundation of cloud security best practice is built on selecting a trusted service provider. You want to partner with a cloud provider who delivers the best in-built security protocols and conforms to the highest levels of industry best practice.
A service provider who extends a marketplace of partners and solutions to you in order to further enhance the security of your deployment.
The mark of a trusted provider is reflected in the range of security compliance and certifications they hold. Something any good provider will make publicly available. For example, all leading providers like Amazon Web Services, Google Cloud and Azure offer transparent access where you can confirm their security compliance and certifications.
Beyond this, there are many factors that go into selecting a trusted provider.
Understand Your Shared Responsibility Model
When partnering with a cloud service provider, and you move your systems and data to the cloud, you enter into a partnership of shared responsibility for security implementation.
A critical part of best practice involves reviewing and understand your shared responsibility. Discovering which security tasks will remain with you and which tasks will now be handled by the provider.
This is a sliding scale depending on whether you’re opting for Software as a Service (SaaS), Platform as a Service (PaaS), Infrastructure as a Service (IaaS), or in an on-premises datacenter.
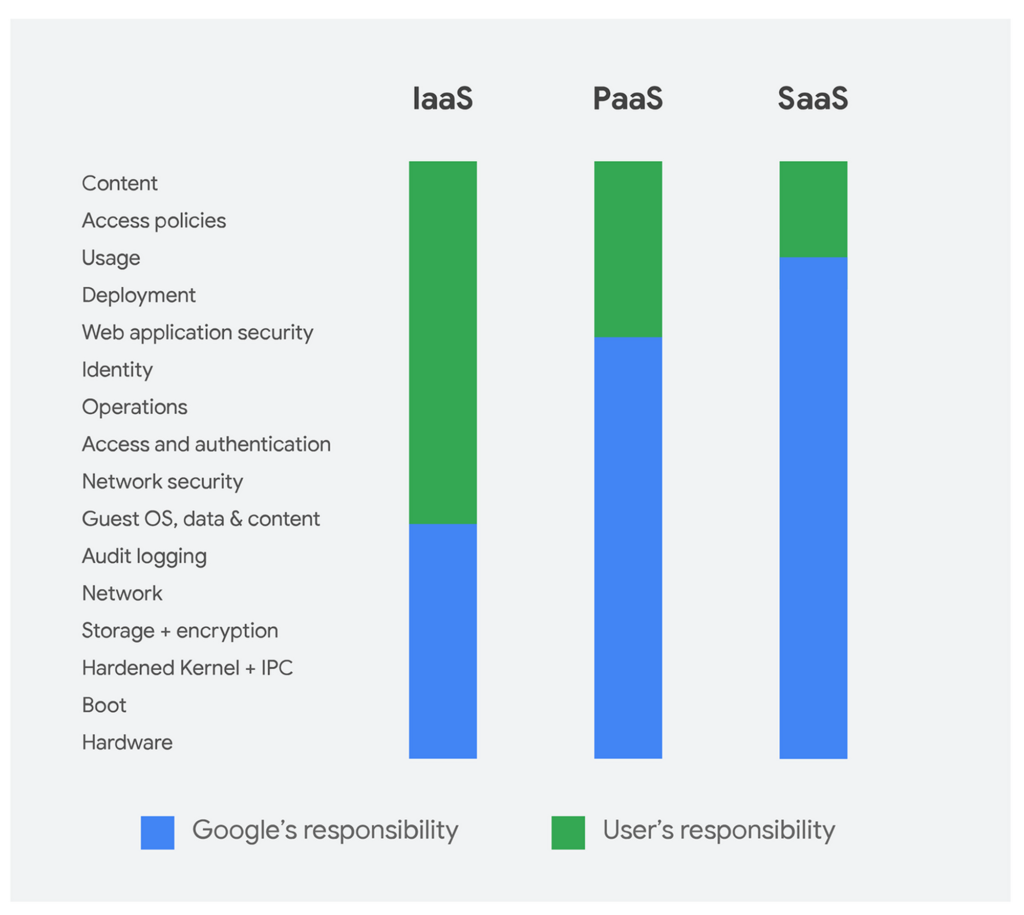
Google Cloud Platform Shared Responsibility Model
Leading cloud service providers like AWS, Azure, Google Cloud Platform, and Alibaba Cloud publish what is known as a shared responsibility model for security. Ensuring transparency and clarity. Make sure you review your cloud service providers shared responsibility model.
Review Your Cloud Provider Contracts and SLAs
You might not think of reviewing your cloud contracts and SLAs as part of security best practice, you should. SLA and cloud service contracts are only a guarantee of service and recourse in the event of an incident.
There is a lot more included in the terms and conditions, annexes, and appendices that can impact your security. A contract can mean the difference between your cloud service provider being responsible for your data and owning it.
According to the McAfee 2019 Cloud Adoption and Risk Report, 62.7% of cloud providers don’t specify that customer data is owned by the customer. This creates a legal grey area where a provider could claim ownership of all your uploaded data.
Check who owns the data and what happens to it if you terminate your services. Also, seek clarity on whether the provider is required to offer visibility into any security events and responses.
If you’re unhappy with elements of the contract, try to negotiate. If any are non-negotiable, you need to determine if agreeing is an acceptable risk to the business. If not, you’ll need to seek out alternative options to mitigate the risk through encryption, monitoring, or even an alternative provider.
Train Your Users
Your users are the first line of defense in secure cloud computing. Their knowledge and application of security practices can be the difference between protecting your system or opening a door for cyber attacks.
As a best practice, make sure you train all your users – staff and stakeholders – who access your systems in secure cloud practices. Make them aware of how to spot malware, identify phishing emails, and the risks of insecure practices.
For more advanced users – such as administrators – directly involved in implementing cloud security, consider industry-specific training and certification. You’ll find a series of recommended cloud security certifications and training later in the guide.
Control User Access
Implementing tight control of user access through policies is another cloud security best practice. Helping you to manage the users that are attempting to access your cloud services.
You should start from a place of zero trust, only affording users access to the systems and data they require, nothing more. To avoid complexity when implementing policies, create well-defined groups with assigned roles to only grant access to chosen resources. You can then add users directly to groups, rather than customizing access for each individual user.
Secure Your User Endpoints
Another element of cloud security best practice is to secure your user endpoints. The majority of users will access your cloud services through web browsers. It’s therefore critical you introduce advanced client-side security to keep your users’ browsers up-to-date and protected from exploits.
You should also consider implementing an endpoint security solution to protect your end-user devices. Vital with the explosion of mobile devices and remote working, where users are increasingly accessing cloud services through devices not owned by the company.
Look for a solution that includes firewalls, antivirus, and internet security tools, mobile device security, and intrusion detection tools.
Maintain Visibility of Your Cloud Services
The use of cloud services can be diverse and fleeting. Many organizations use multiple cloud services across a range of providers and geographies. With research suggesting cloud resources have an average lifespan of 2 hours.
This kind of behavior creates blind spots in your cloud environment. If you can’t see it, you can’t secure it.
Make sure you implement a cloud security solution that offers visibility of your entire ecosystem. You can then monitor and protect cloud usage across all your disparate resources, projects and regions through one single portal. This visibility will help you implement granular security policies and mitigate a wide range of risks.
Implement Encryption
Encryption of your data is a security best practice regardless of location, critical once you move to the cloud. Using cloud services, you expose your data to increased risk by storing it on a third-party platform and sending it back and forth between your network and the cloud service.
Ensure you implement the highest levels of encryption for data both in transit and at rest. You should also consider using your own encryption solutions before uploading data to the cloud, using your own encryption keys to maintain full control.
A cloud provider might offer built-in encryption services to protect your data from outside parties, but it affords them access to your encryption keys.
Implement a Strong Password Security Policy
A strong password security policy is best practice regardless of the service you are accessing. Implementing the strongest policy possible is an important element in preventing unauthorized access.
As a minimum requirement, all passwords should require one upper-case letter, one lower-case letter, one number, one symbol, and a minimum of 14 characters. Enforce that users update their password every 90 days and set it so the system remembers the last 24 passwords.
A password policy like this will stop users from creating simple passwords, across multiple devices, and defend against most brute force attacks.
As an additional layer of security best practice and protection, you should also implement multi-factor authentication. Requiring the user to add two – or more – pieces of evidence to authenticate their identity.
Use a Cloud Access Security Broker (CASB)
The use of a CASB is fast becoming a central tool to implement cloud security best practice. It’s software sitting between you and your cloud service provider(s) to extend your security controls into the cloud.
A CASB offers you a sophisticated cloud security toolset to provide visibility of your cloud ecosystem, enforce data security policies, implement threat identification and protection, and maintain compliance.


